900+ Kunden vertrauen der besten Software für
Informationssicherheit, Business Continuity und Datenschutz.







Smart Content AI: Die beste generative KI-Lösung im GRC-Bereich
- Unsere KI generiert, optimiert und verknüpft beinahe alle GRC-relevante Daten inkl. Texte und Beschreibungen
- Maßgenschneiderte Inhalte basierend auf Ihrer Organisation (u.a. Branche, Organisationsstruktur, Geschäftstätigkeit, Standorte, relevante Standards)
- Effizienzgewinn > 80%
Kostenfreies NIS-2 Tool: Sind Sie betroffen?
Die Umsetzung von NIS-2 in nationales Recht verpflichtet allein in Deutschland über 25.000 zusätzliche Organisationen zu strengen Sicherheitsmaßnahmen. Viele Unternehmen stehen vor der Herausforderung, ihre eigene Betroffenheit und die daraus resultierenden Pflichten im Risikomanagement präzise einzustufen.
Prüfen Sie Ihren Status kostenfrei in wenigen Minuten!
Unser kostenloses NIS-2 Betroffenheitstool bietet Ihnen eine schnelle und fundierte erste Orientierung. Sie erhalten kostenfrei eine Ersteinschätzung zu Betroffenheit und zusätzlich einen individuellen Risiko-Score, Handlungsempfehlungen und Management-Report!

Die erste digital souveräne GRC Lösung mit STACKIT
1 Plattform. 5 Module. Maximale Resilienz und digitale Souveränität.
Die GRC Cloud ist eine intelligente Plattform, die Ihre Teams verbindet, Risiken minimiert und Ihr Unternehmen stärkt. Dabei verfolgen wir einen integrierten Ansatz und vereinen Management von Datenschutz und Informationssicherheit in einer Plattform.
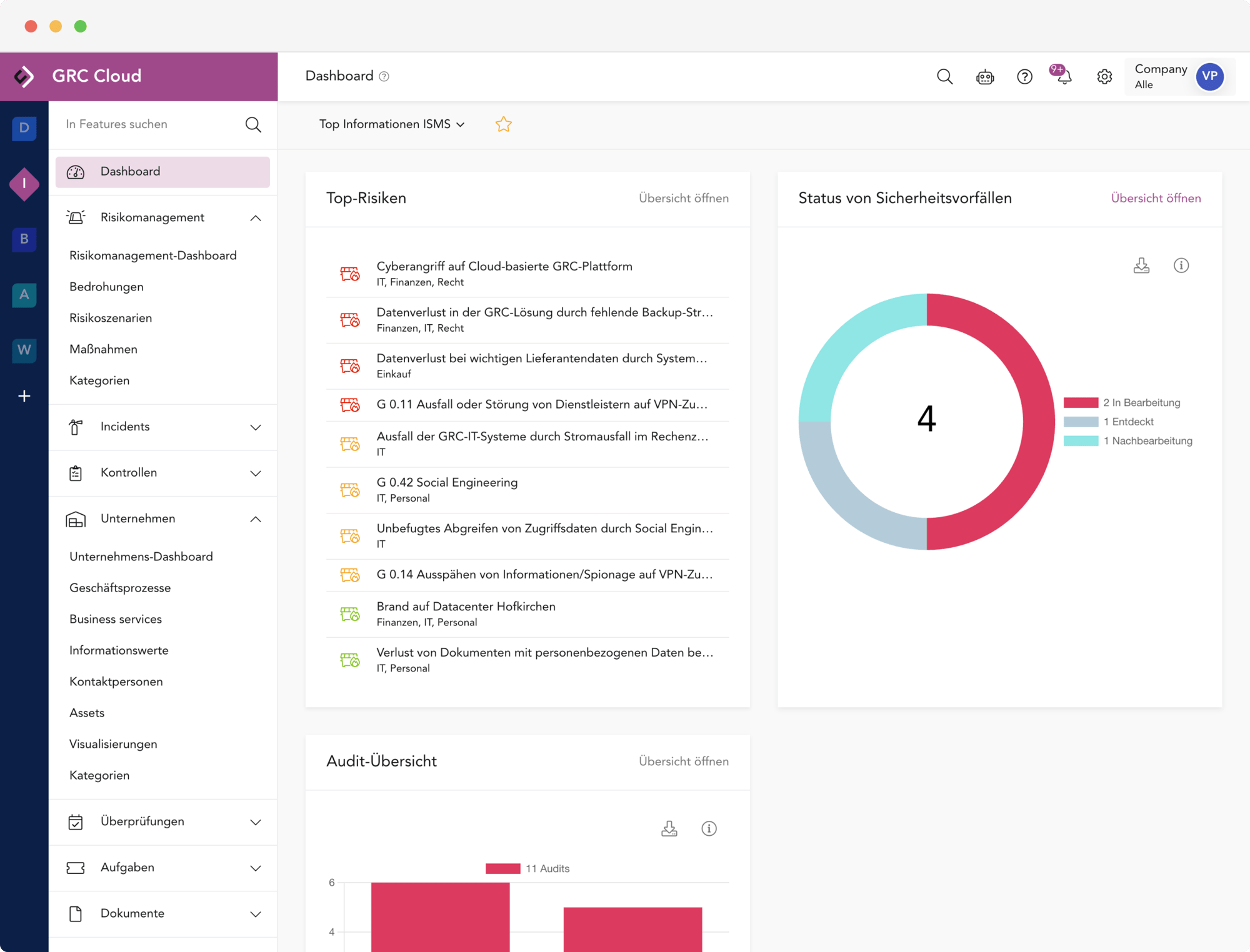
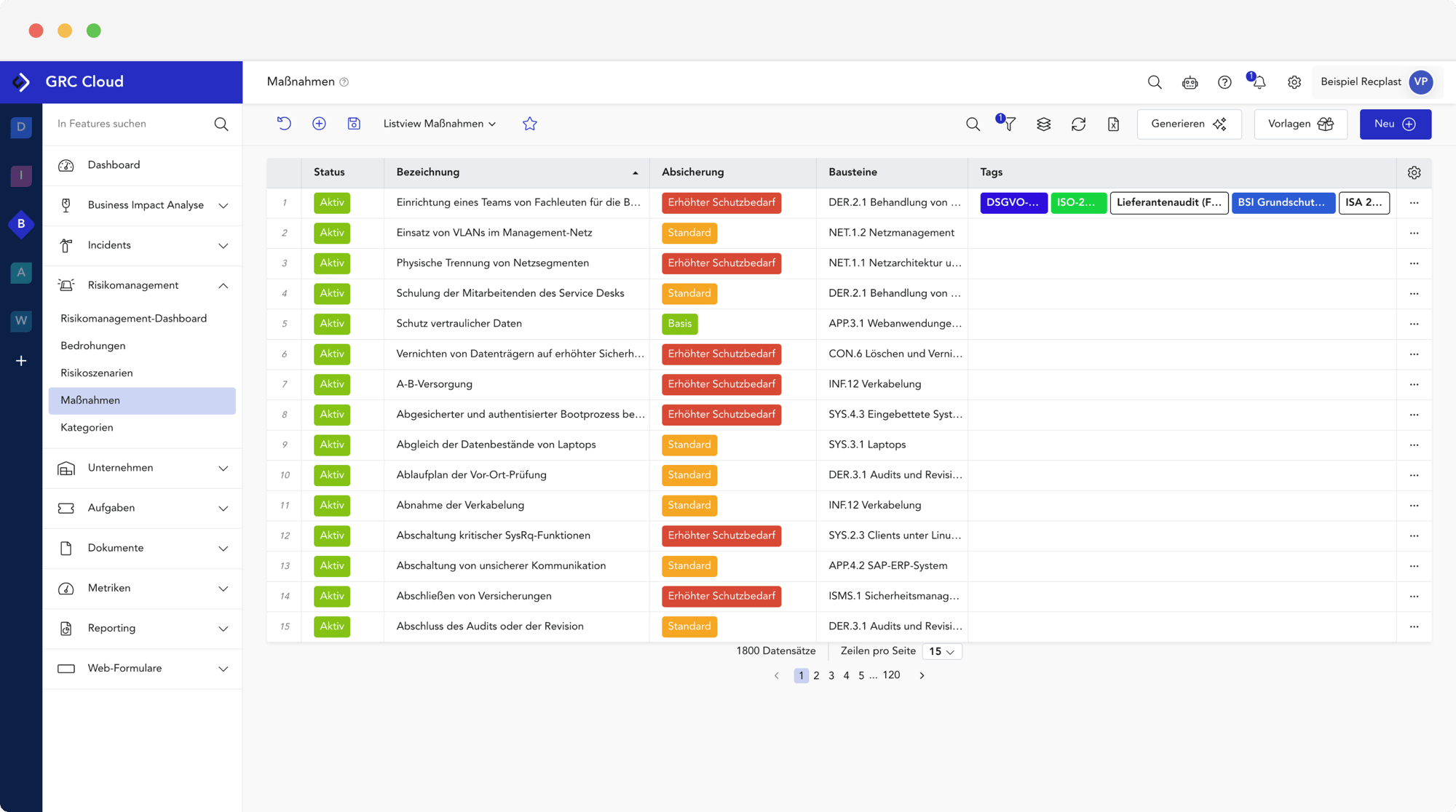
- Mandantenfähigkeit mit Vererbung: Top-Down & Bottom-Up (inkl. Vorlagenmandanten)
- Hochmoderne UI und beste Benutzbarkeit
- Generative KI inkl. Berechtigungskonzept
- Mehrsprachigkeit und automatische Übersetzung
- Granulares Rollen- und Rechtemanagement
- Aufgaben-, Projekt- und Workflow-Management
- Einmaliges Erfassen von Prozesse, Daten, Assets usw. und Verwendung in allen relavanten Modulen
5 Module für Ihren individuellen Bedarf

- Akai - Smart Content AI
- Multi-Stage-Approval Workflow
- Multi-Faktor-Authentifizierung (MFA)
- Single Sign-on (SSO)
- Autoprovisioning
Ihre GRC-Zukunft startet hier: Kontaktieren Sie uns!
Sicher. Innovativ. Digital souverän.
100% Entwicklung
in AT und DE
DE & AT Hosting bei STACKIT
Digitale Souveränität
99,995%
Verfügbarkeit
217 Updates & Verbesserungen
an unserer Software allein in 2024
Unterstützte Frameworks
Regulatorische Anforderungen an Unternehmen sind heterogen. Daher unterstützen wir mit einer Vielzahl von Katalogen / Frameworks / Normen / Richtlinien für Ihren individuellen Use-Case.

ISO 27001
ISO 27019
ISO 27701
ISO 22301
EU NIS-2
DORA
BSI 200-1
BSI 200-2
BSI 200-3
BSI 200-4
ITGS Kompendium
BSI C5
VDA ISA
SDM (DSGVO)
B3S Gesundheit
B3S Energie
PCI DSS
Weitere Kataloge jederzeit auf Anfrage.
This event has passed!
Treffen Sie uns auf der IT-SA 2025!
00
Tage
00
Stunden
00
Minuten
00
Sekunden

Die IT-SA ist eine weltweit größten Dialogplattformen für branchenspezifische IT-Security-Lösungen und AKARION ist dabei.
Unser Messeteam zeigt Ihnen an unserem Stand unsere neuesten Innovationen, u.a. unsere neue Smart Content AI. An zwei Demo-Stationen können Sie sich jederzeit selbst überzeugen, dass die AKARION GRC Cloud die beste GRC-Software am Markt ist.
Halle 9 | Stand 112
Gerne können Sie schon vorher einen Termin mit uns vereinbaren!
Exzellenz ist kein Zufall.
Deshalb stellen wir uns regelmäßig den strengsten Prüfungen und engagieren uns dort, wo die Standards von morgen entwickelt werden. Die hier aufgeführten Zertifikate und Mitgliedschaften sind für uns eine Selbstverständlichkeit – und für Sie die Garantie, mit einem Partner auf Augenhöhe zu arbeiten.

Partner der BSI Allianz für Cyber-Sicherheit
Mitglied im Bitkom e. V.

Die Akarion GmbH ist ISO/IEC 27001:2022 zertifiziert

Lizensierter BSI
IT-Grundschutz-Tool Anbieter
Jetzt wechseln: Ihre Software bekommt Updates? Unsere bekommt Upgrades.
Egal ob Sie sich mit einer Dokumentensammlung behelfen oder bereits eine Software im Einsatz haben: der Wechsel zur AKARION GRC Cloud ist einfach, schnell und wird eng von uns begleitet.
UI & UX aus der Steinzeit? Nicht bei uns.
Schluss mit veralteten Oberflächen und endlosen Klicks. Unsere GRC-Plattform überzeugt durch herausragende Usability und ein modernes Design.
Eine Lösung für alle, statt Chaos für jeden.
Anstelle teurer Insellösungen bieten wir eine mandantenfähige und skalierbare Plattform für alle Ihre Standorte unabhängig vom Reifegrad.
Spüren Sie den Unterschied, nicht den Aufwand.
Unsere GRC Cloud bekommt Upgrades statt Updates. Als echte SaaS-Lösung mit KI entwickeln wir uns wöchentlich weiter und liefern Ihnen kontinuierlich Innovationen.
98% unserer Kunden verlängern Ihre Lizenzen.

Marco van Schoonderwaldt
Experte Info-Sec. Management
Die Wahl fiel auf die AKARION GRC Cloud – eine Entscheidung, die nicht nur den aktuellen Bedarf abdeckt, sondern auch die wachsenden Anforderungen der Zukunft begleitet, insbesondere im Hinblick auf die Accessibility.


Frank Peter
Leiter Datenschutz und Datensicherheit
Mit der AKARION GRC Cloud können unsere Berater Datenschutz und Informationssicherheit effektiv verzahnen und so die Anforderungen unserer Kunden optimal erfüllen.Zugleich sind wir ein ganzes Stück effizienter geworden. Eine Win-Win-Situation für alle Beteiligten.


Christian Bockrath
Informationssicherheits-beauftragter
Endlich habe ich eine Software entdeckt, das es mir ermöglicht, Risikoanalysen umfassend durchzuführen und dabei sowohl die Informationssicherheit als auch den Datenschutz zu berücksichtigen. Die daraus resultierenden Synergieeffekte lassen sich optimal nutzen.


Beatrice Dietrichsteiner
CISO and Project Success Manager
Die AKARION GRC Cloud hilft uns schnell und einfach Geschäftsprozesse abzubilden, den Schutzbedarf zu bestimmen. Ergänzt durch clevere Funktionalitäten, die auch die Business Continuity stärken, können SLA/OLA Untererfüllungen identifiziert werden. Gerade die Workflows sind für uns unverzichtbar geworden.


Theresa Steinmetz
Informationssicherheits-Risikomanagerin
Unser wichtigstes Gut sind Daten. Diese müssen geschützt werden.Durch die GRC Cloud verzeichnet sich im Vergleich mit der alten Excel-Lösung eine immense Zeitersparnis. Ich würde diese mit etwa 60 Prozent beziffern. Bei der Usability sind es sogar 100 Prozent.


Andreas Bögemann
Geschäftsführer
Durch die automatischen Überprüfungspläne können systematische sowie regelmäßige Überprüfungen abgehalten werden. Alle wichtigen Informationen werden hierbei automatisch, klar und übersichtlich im Dashboard des ISMS-Moduls dargestellt. Dies reduziert unseren Aufwand gegenüber einer manuellen Überprüfung ungemein!


Daniel Holzer
Geschäftsführer
Als führender EDV-Anbieter der oberösterreichischen Gemeinden benötigen wir eine Lösung, die praxisnah und intuitiv ist, um die komplexen Strukturen der öffentlichen Verwaltung abzubilden. Die AKARION GRC Cloud hilft uns dabei, die Dokumentation unserer Gemeinden aktuell zu halten und jährliche Audits effizient durchzuführen.


Alexander Dressler
Data Protection Manager
Unser wichtigstes Gut sind Daten. Diese müssen geschützt werden.Durch die GRC Cloud verzeichnet sich im Vergleich mit der alten Excel-Lösung eine immense Zeitersparnis. Ich würde diese mit etwa 60 Prozent beziffern. Bei der Usabilität sind es sogar 100 Prozent


Tobias Schmidt
Security & Compliance
Das Gesamtpaket, das AKARION mit seiner GRC Cloud in den Punkten Datenschutz, Informationssicherheit, Risk Management und Audit anbietet, hat einfach gepasst. Die GRC Cloud ist das zentrale Element, mit dem die dezentralen Systeme verknüpft sind. Dies hilft uns immens bei der Lokalisierung notwendiger Informationen.
















