
AKARION ist
Mit unserer Cloud-Software können Sie Ihre Themen GRC und Informationssicherheit sicher und ganzheitlich angehen. AKARION macht Ihre Geschäfts- und Arbeitsabläufe einfacher, schneller und effizienter.





















































































Unsere Lösungen
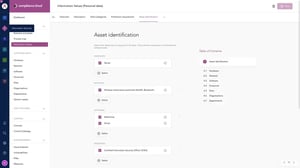
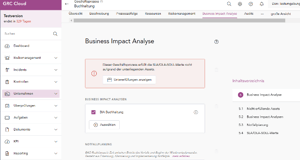
Viel Regulierung - eine Software! Mit GRC Experten haben wir eine Lösung geschaffen, mit der Sie Synergien zwischen Governance, Risikomanagement, Compliance und Informationssicherheit Fachbereichen ganz einfach heben können. Mit drei Hauptmodulen und zusätzlichen Features ermöglicht Ihnen die GRC Cloud ein ganzheitliches GRC-Management. Schneller, einfacher und effizienter!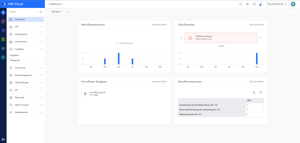



"Der größte Unterschied zu anderen Anbietern liegt in der Modularität der Lösung, die aus meiner Sicht viele Vorteile bietet, sowie dem sehr engen, persönlichen Kontakt und der intensiven Betreuung während der Installations- und Einführungsphase. Besonders überrascht war ich von der doch sehr intuitiven Anwendung."

ISMS in Versorgungsunternehmen (Case Study)
Effiziente Implementierung der Akarion GRC Cloud
Ein ISMS, das mit den Herausforderungen wächst: Die Stadtwerke Düsseldorf AG hat frühzeitig erkannt, dass Informationssicherheit kein statisches Konzept ist, sondern eine kontinuierliche Entwicklung erfordert. Lesen Sie in unserer Case Study, wie das Unternehmen sein ISMS modernisiert, Cyberrisiken reduziert und eine nachhaltige Sicherheitsstrategie etabliert hat.
jetzt kostenlos downloaden
Neue Blog Beiträge
Wer steckt hinter AKARION
Ein dynamisches Team, das mit Leidenschaft und herausragendem Teamgeist an der Entwicklung und Durchsetzung von innovativen und modernsten GRC Lösungen arbeitet.





