
Information Security Module: an ISMS tool developed by Akarion
Concrete measures to improve Information Security and Cyber Resilience
The most efficient management of information security risks
Fulfilment of standards such as ISO 27001, German BSI Grundschutz, B3S and NIS2.
Supported by state-of-the-art workflows for audits and more







Information Security Module
Do you spend more time on documentation in Excel and Word than on the actual implementation of your ISMS?
With the Akarion GRC Cloud's Information Security module, you can optimise your time with numerous intelligent connections and innovative processes.

A smart ISMS tool designed around your efficiency
The Information Security module provides you with the tools, documentation and knowledge you need to manage information security holistically.
Concrete results
- Simplified & streamlined documentation
- Improvement of information security in the organisation
- High cyber resilience according to the newest compliance standards
AKARION allows us to organise our company in the best possible way within the tool.
We can quickly and easily map the business processes, determine the protection requirements and model the dependency chains of the assets, which also inherit the protection requirements directly from the business process. SLA/OLA breaches can be identified, complemented by smart functionality that also strengthens and serves business continuity. These are images and workflows that have become indispensable for us.

Through my work as an Information Security Risk Manager, I am very familiar with the functionality of risk management in the ISMS tool through my daily work. I particularly appreciate the simple handling of the sophisticated complexity and the visualisation of the interrelationships, from an asset to a complex business process. The information gained is of great benefit to us. I can highly recommend Akarion and the ISMS module in particular, as I am convinced of the user-friendly implementation of complex information security requirements.

With the help of AKARION, we can now efficiently map the necessary inspections. Thanks to the automatic audit plans, systematic and regular audits can be carried out according to a defined interval. All important information is displayed automatically, clearly and concisely in the dashboard of the ISMS module. This greatly reduces our workload compared to manual checks!

I have finally found a tool that allows me to carry out comprehensive risk analyses, taking into account both information security and data protection. The resulting synergies can be exploited to the full. In addition, I use a detailed catalogue of measures that specifically addresses various risks and vulnerabilities and rounds off the whole process perfectly.

Our vision for information security for the future
Information Security made holistic
In your day-to-day work as an information security officer, have you ever noticed that information security management rarely stands alone? The basics of information security are very similar, often identical, to those of data protection or emergency management. It is therefore best to use one tool for all subjects. With our Information Security module, you can see how you can combine all relevant compliance management topics into one and thus reap the benefits of digitalisation.
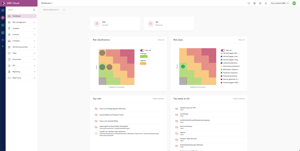
Identify and respond to risks quickly
You already have an information security management system in place and an Information Security Officer (ISO). However, your IT infrastructure and your interactions with external parties are very complex. This makes it difficult for your organisation to keep track of all the interdependencies between the information assets to be protected (e.g. confidential business documents) and the resources used (i.e. assets such as software and hardware), and to quickly identify risks and the necessary measures. With our intelligent ISMS with built-in inheritance system, you will not only build your ISM comprehensively, but also sustainably and effectively.
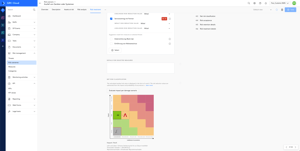
Perfectly prepared for the certification process
Whether it is ISO 27001 or VDA ISA, you need to prepare yourself and your organisation for certification and the subsequent surveillance audits. The key to successful and sustainable certification is to have all relevant control and risk catalogues in view and to document everything according to PDCA. Use the ISMS module of the GRC Cloud and make your information security management audit-proof through continuous documentation.

Keep your most important assets in one place. You can see important relationships at a glance, such as whether records are referenced or have recently changed. Capture and document your organisation's assets (hardware, software, people, etc.) using a wide range of templates. Personalise values for protection objectives, risk categories and matrices, assessment periods, etc. to tailor the module to your organisation and ISM methodology.
Identify and document existing risks (e.g. fire) and address them with appropriate measures (e.g. fire extinguishers). You can also define and visualise the protection needs of your information assets based on requirements for confidentiality, integrity, availability, or other protection objectives such as authenticity.
Identify your organisation's critical vulnerabilities and risks, and document the actions you take to address them and their impact on risk. As you analyse and manage risks, you can efficiently record them and automatically escalate them to lower levels.
Capture all your business processes at a glance by documenting all stages, such as sub-processes and protection requirements analyses. This gives you a comprehensive and easy-to-understand visualisation of all your business processes.
Stay on top of security incidents at all times. Efficient workflow management allows you to assign tasks to incidents. Keep track of not only open tasks, but also changes to the incident and the current risk posture of your organisation.
Add-ons for the Information Security module
Discover our two add-ons that allow you to take GRC to the next level for your organisation and your customers.
